Simplify the oversight and management of your cybersecurity program with BW Secure™.
Our one-stop shop for all cyber activities platform integrates advisory, managed services, and your technology security stack to offer a seamless way to oversee all of the work we do for you. Proactively meet your cybersecurity needs and know exactly where your program stands with near real-time executive reporting dashboard.
Cybersecurity Program Oversight
3rd Party Risk Management
Historical Trends for Program Health
Regulatory Compliance Readiness
Document Management
Customizable Dashboards
Vulnerability Scanning
Security Roadmap
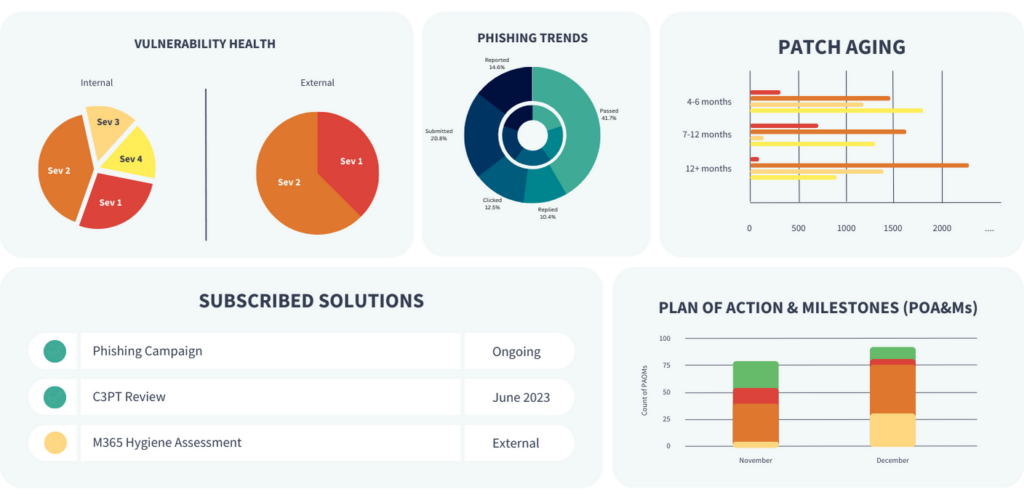
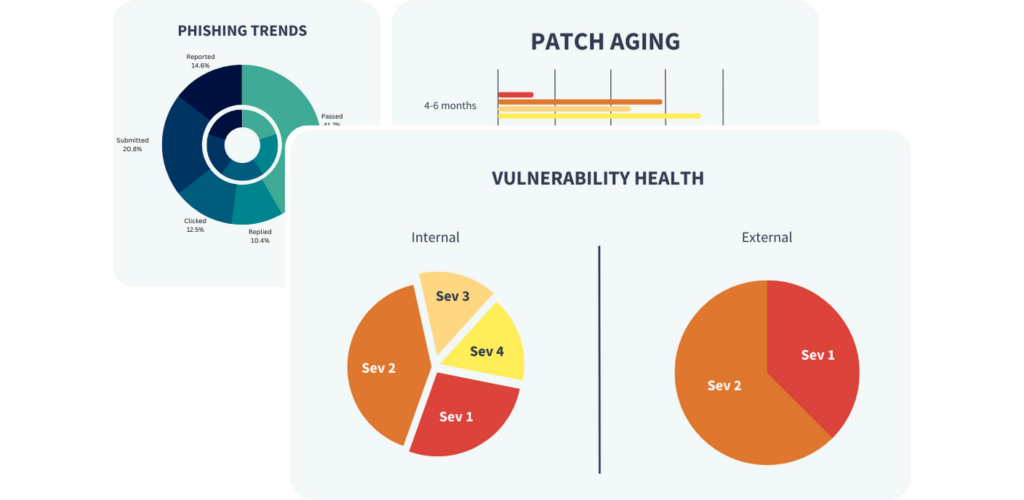
Vulnerability Management + Dark Web Monitoring
Address cyber risks quickly and easily.
BW Secure™ offers seamless and continuous vulnerability management, enabling you to quickly identify and remediate cyber risks such as missing patches, software vulnerabilities, and more.
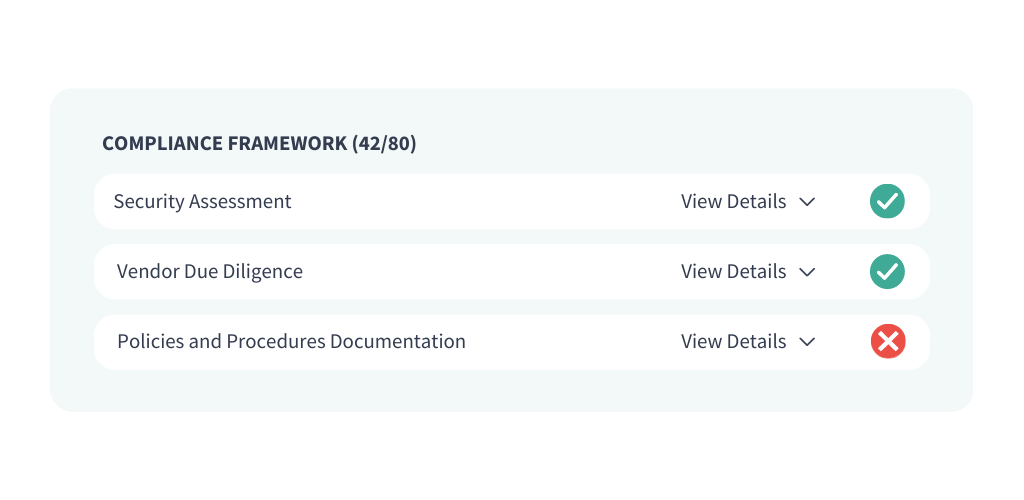
Regulatory Compliance Readiness
Save time and energy while proactively meeting compliance mandates.
Consolidate compliance efforts and simplify document management across many frameworks such as SEC, NFA, FINRA, CFTC, HIPAA, HITRUST, SOC, and CMMC .
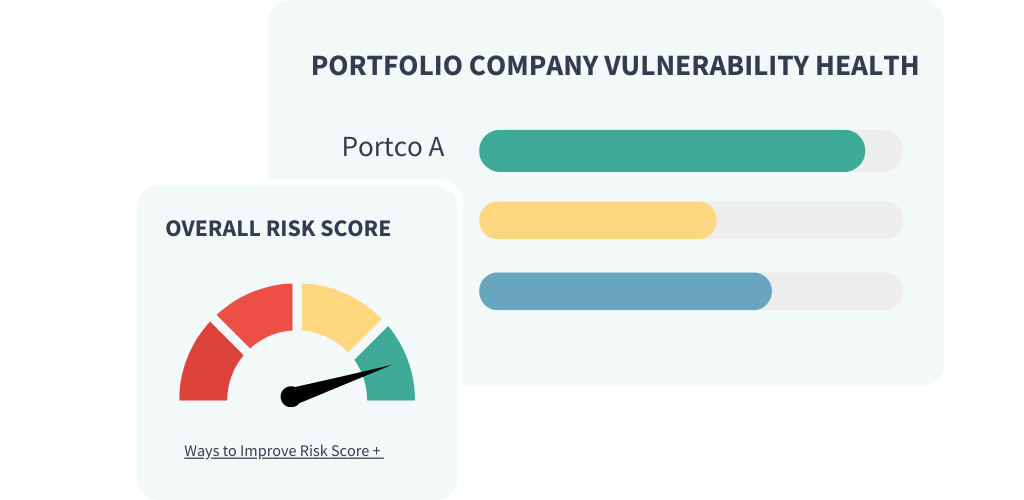
Reporting
Measure security health across your business and your portfolio.
Get clarity into the health of your cybersecurity program with simple dashboards built to simplify the complexity of measuring security maturity over time.
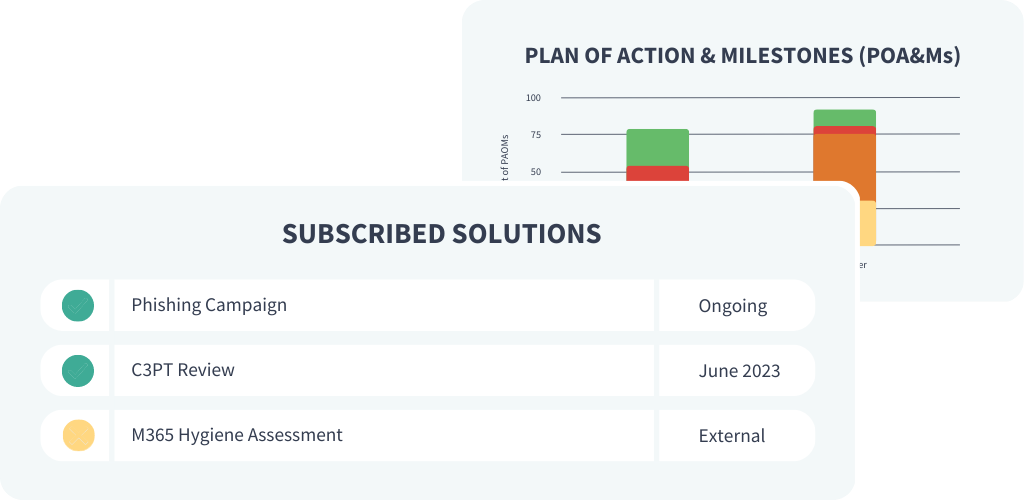
3rd Party Risk Management
Manage vendor oversight.
Meet compliance mandates around vendor oversight and manage vendor due diligence. Simplify project management across teams and vendors.
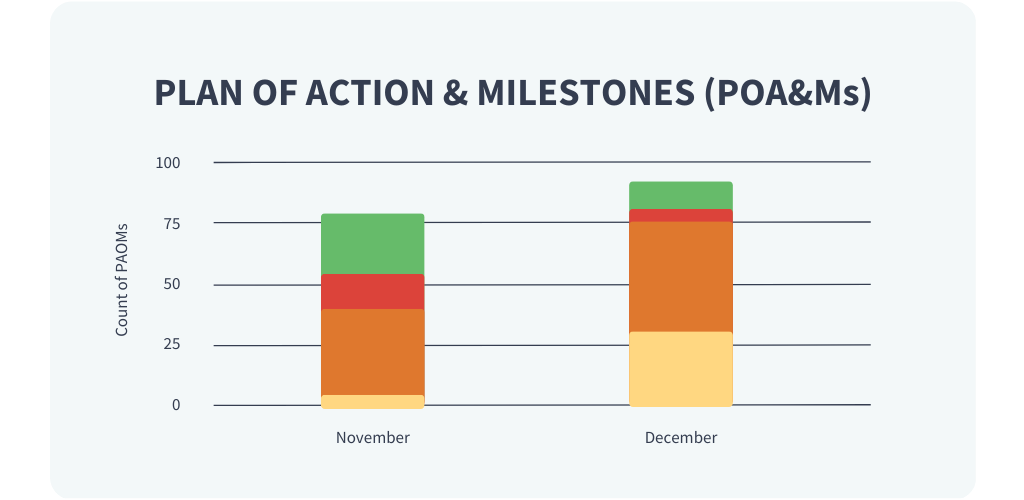
Plan of Action + Milestones
Know where you stand AND what comes next.
Get a clear view of the progress you’ve made to date and see next steps.
Cybersecurity Program Overview
BW Secure™ provides a single consolidated environment to visualize and summarize your entire cyber program, making it accessible to everyone from CEO to IT Director.
- IT security policy compliance + management scorecard
- Supports cyber program governance
- Monitor health of internal and external networks
- Simple, executive-level reporting
- Granular internal access controls
- Secure vendor access


